↘ Reduce Spying iPhone
How can you reduce the threat of spying on your iPhone?
How can you reduce the threat of spying on your iPhone?
According to CISA newly identified Truebot malware variants against organizations in the United States and Canada.
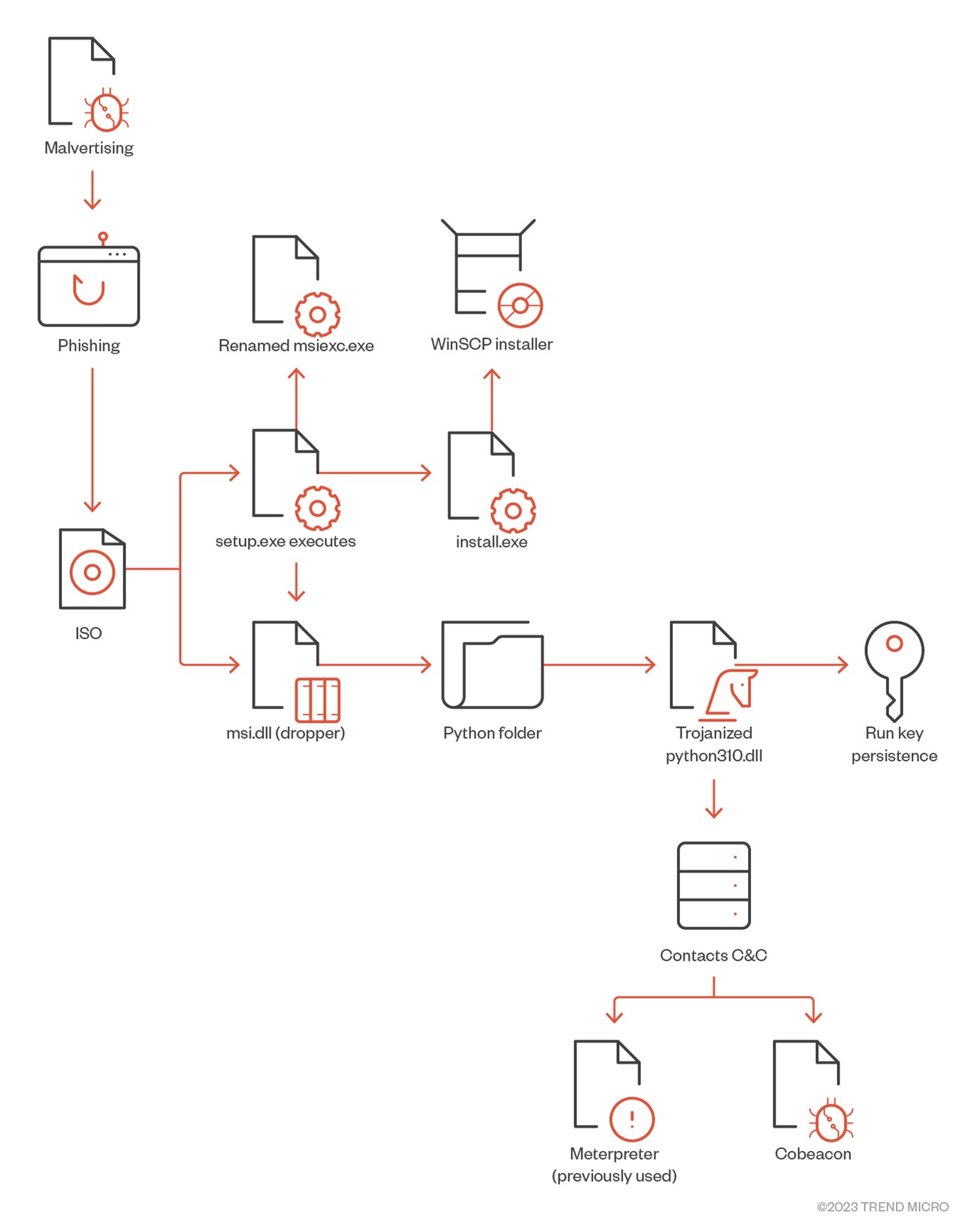
Advertising platforms like Google Ads enable businesses to display advertisements to target audiences to boost traffic and increase sales. Malware distributors abuse the same functionality in a technique known as malvertising, where chosen keywords are hijacked to display malicious ads that lure unsuspecting search engine users into downloading certain types of malware.
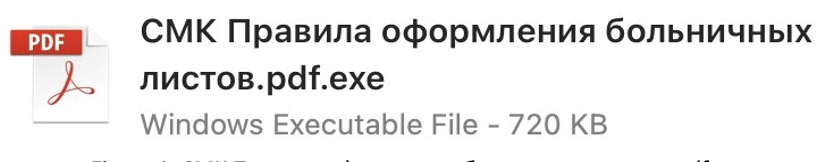
FortiGuard Labs recently came across files that look suspicious, even during a cursory review. Our subsequent investigation confirmed that the files are malicious and revealed there is more to them than meets the eye: they are a previously unseen infostealer we have named “ThirdEye”. While this malware is not considered sophisticated, it’s designed to steal various information from compromised machines that can be used as stepping-stones for future attacks.
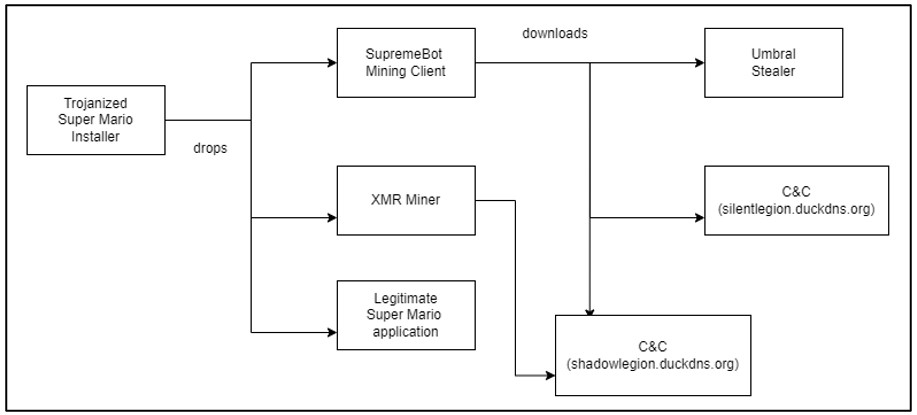
Trojanized Super Mario Game Installer Spreads SupremeBot Malware
OpenBLD.net DNS Mitigated Influence from new Microsoft Encrypted Restricted Permission Messages Deliver Phishing