↘ Prevent MS Encrypted Phishing
OpenBLD.net DNS Mitigated Influence from new Microsoft Encrypted Restricted Permission Messages Deliver Phishing
OpenBLD.net DNS Mitigated Influence from new Microsoft Encrypted Restricted Permission Messages Deliver Phishing
The rise of phishing activities has taken the top spot in attacks targeting end-users and organizations. Among the various forms of phishing attacks, there's one known as "SMiShing" attacks, which target users through SMS messages.
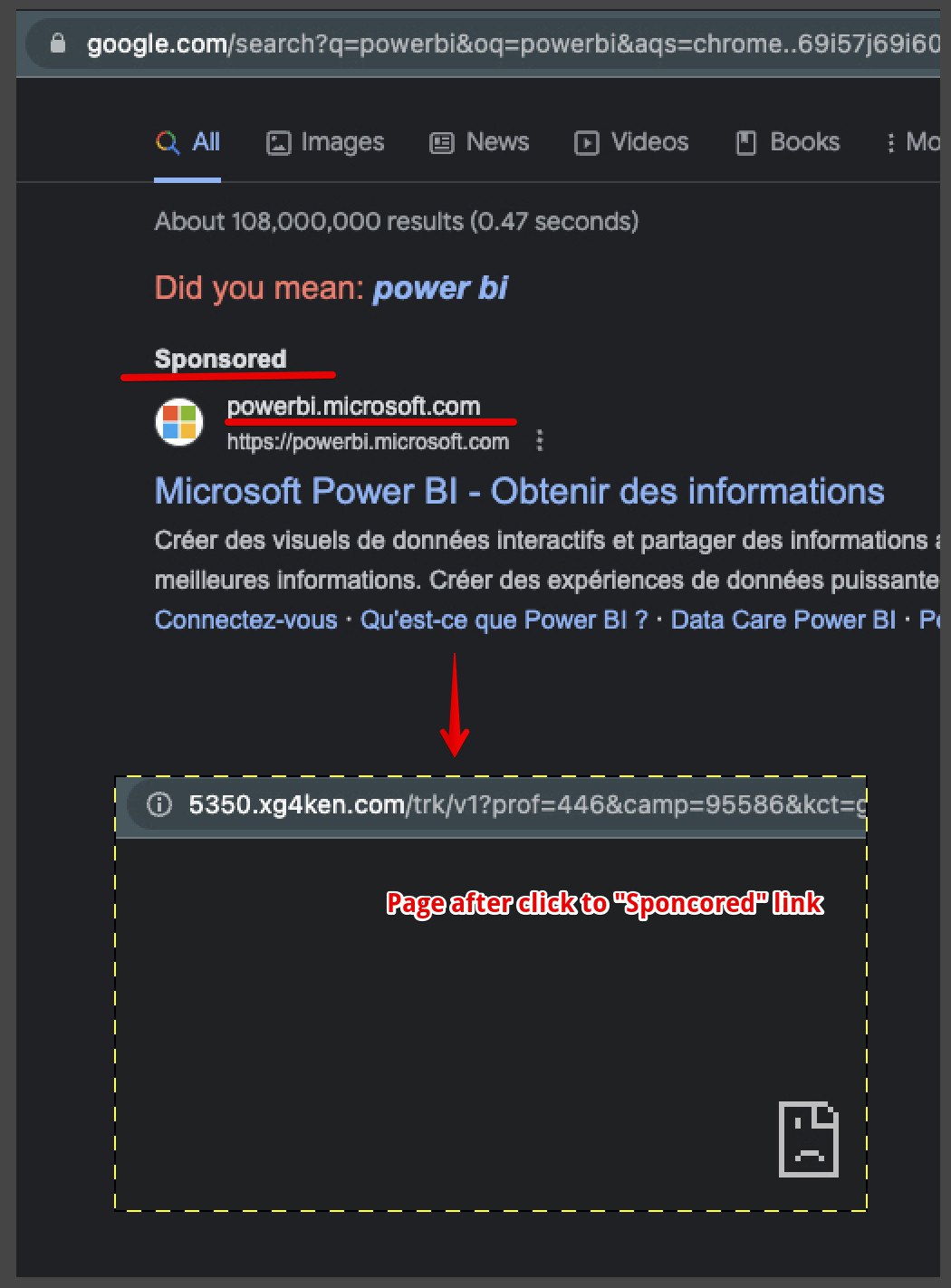
Today I discovered a new malicious company that spreads through of Google Ads side...
Malvertising seems to be enjoying a renaissance as of late, whether it is from ads on search engine results pages or via popular websites. Because browsers are more secure today than they were 5 or 10 years ago, the attacks that we are seeing all involve some form of social engineering.
A threat actor is using malicious ads to redirect users to what looks like a Windows security update. The scheme is very well designed as it relies on the web browser to display a full screen animation that very much resembles what you'd expect from Microsoft...