🟢️️️️️️ OpenBLD.net New server in Kazakhstan

I hear a lot of good reviews from people about the new Yandex cloud in Kazakhstan 🇰🇿. And so, having saved up some money and received a small deposit from Yandex, I decided to try the cloud.

I hear a lot of good reviews from people about the new Yandex cloud in Kazakhstan 🇰🇿. And so, having saved up some money and received a small deposit from Yandex, I decided to try the cloud.

Today wll deploy new zBLD backend release in to production environment.

Speed directly affects our time; the faster the service works, the faster your Internet works, thus saving your time and the time of consuming server resources.
Time is life, time is money, time is the most important resource in the world, which we must treat with care.

👨👩👧👦 OpenBLD.net - Caring for Children
Understanding that advertisements are junk information for a child's brain, I also recognize that "adult content" is even more unacceptable for minors.
This includes:
Starting today, I'm launching a new server in test mode with filtering for this type of content.

OISD it is one of better projects aimed to reduce internet noise. You can use OISD for own purposes, in your DNS server, or you can use it in OpenBLD.net as a ready-made solution.
The blocklist prevents your devices from connecting to unwanted or harmful domains. It reduces ads, decreases the risk of malware, and enhances privacy. You can see FAQ and other details on the official OISD website.
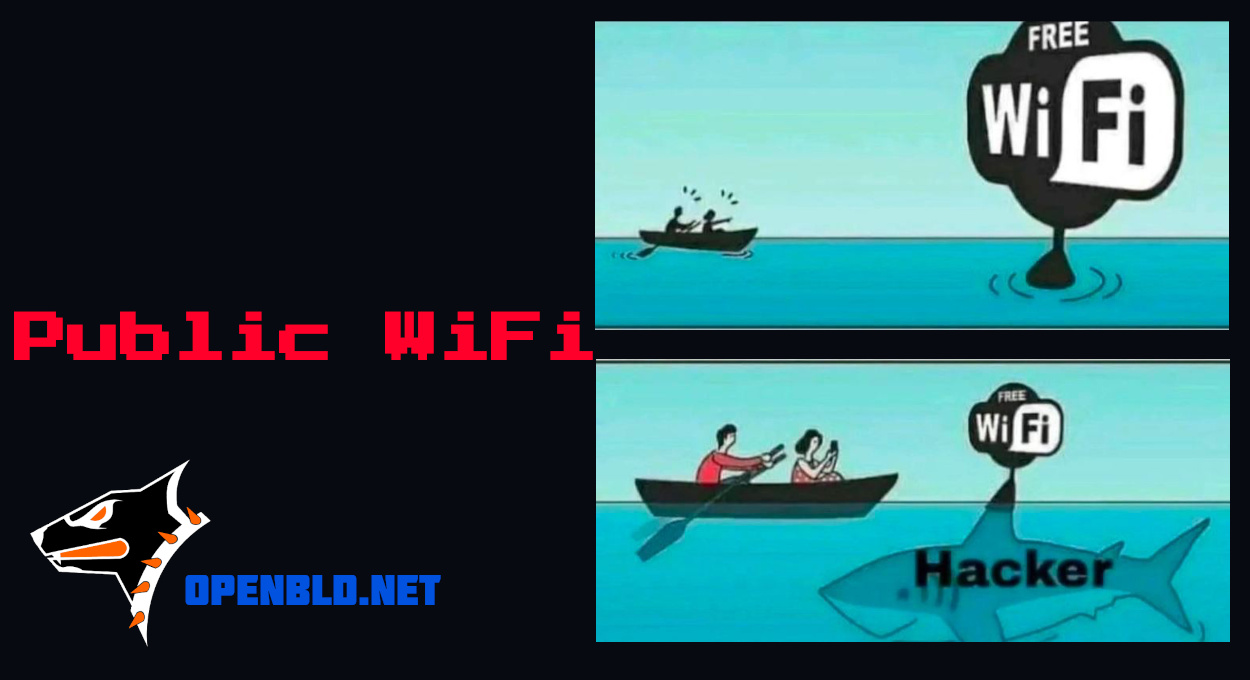
Wi-Fi is a wireless communication technology that allows devices to connect to the internet and exchange data without using wired connections. Public Wi-Fi networks, available everywhere in public places such as cafes, airports, hotels, and shopping malls, provide users with a convenient way to access the internet anytime. However, such networks can pose a security threat as they are typically not password-protected and can be easily compromised by attackers to intercept data or launch attacks on users' devices.